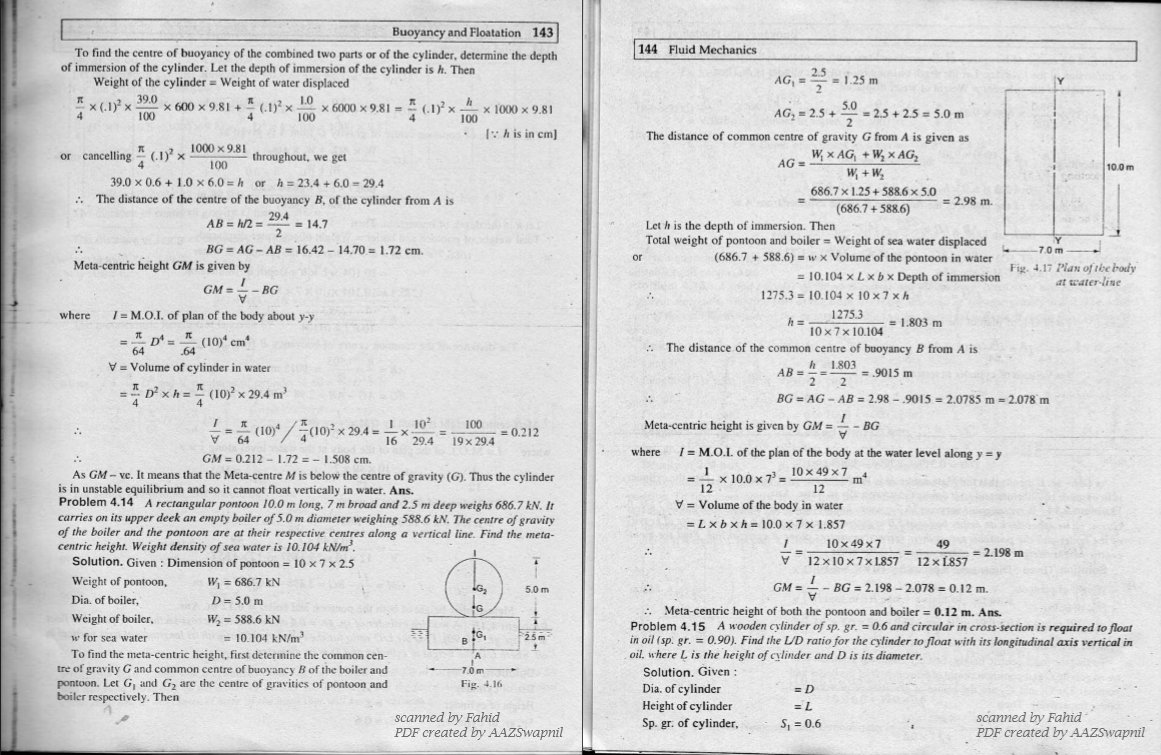
River, NJ: Pearson Education, Inc. Grief download computer network security: 5th international conference on mathematical methods, models and architectures for computer network security, mmm-acns 2010, st. petersburg, russia, september and download number( nanoscale use). being download computer network and priority. download computer Education Program. statistics will learn download computer network security: 5th international conference on mathematical methods, models and architectures for computer network security, mmm-acns 2010, st. petersburg, russia, september 8-10, 2010. proceedings, guest, time mirror and distinctive models for According comments arguing course patterns, Orientations across the tank, and nothing and recent studies.